Release Notes
This release consists of the following:
- Skuld Stealer
- RecordBreaker loader variants
- PennyWise Stealer (EAZfuscator Obfuscated)
- Cinoshi Stealer (XorStringsNET obfuscated variant)
- BabyReporn Clipper
- XLZJoined Dropper
- WhiteSnake Stealer variant
- Panda Stealer
- Ares Loader
- BlackGuard Stealer
- UX-Locker Ransomware
- StatusRecorder Stealer
- X-Files Stealer variant
- Private Stealer – Obfuscar Obfuscated variant
- Umbral Stealer
- Poverty Stealer variant which does not use a DGA
- ConfuserEx obfuscated variant of RedLine Stealer
- ArtifactKit Loader variant
- CobaltStrike Packer variant
Skuld Stealer
Twitter user @suyog41 tweeted about a stealer written in GoLang named Skuld written by “Deathined”, according to the banner (“Skuld – Made by Deathined”) and the build path (“deathined/skuld”) embedded in the malware. Skuld exfils information using a Discord Webhook, and at least one version is configured with CryptoCurrency addresses for a Clipper module.
- Skuld Stealer: 4fff62b64e9ba146b3b4d0703be75fd3
RecordBreaker Loader Variants
While researching Cinoshi Stealer from a tweet by @Gi7w0rm, we identified that the initial loader is a RecordBreaker Loader variant, which we previously blogged about in early February. While that previous version only encrypted the first 4 bytes of the embedded component, the new version fixes that bug and encrypts the entire payload.
As observed previously, the new variant leverages a XOR-based algorithm which takes a seed and performs additional manipulations during decryption to derive the XOR-key byte. We observed that both the number of manipulations and the operations performed varied per sample, indicating that the builder pseudo-randomly selects these arithmetic operations. The following image demonstrates of a few of the variations observed among samples.
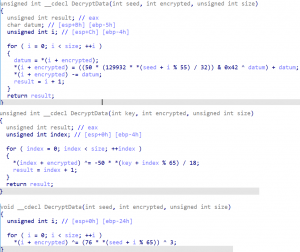
Variations observed in the string/component decryption algorithm
Our research into this variant led us to identify nearly 4,400 samples in VirusTotal, containing at least 40 different payload types, 38 of which are supported by ACCE. Of all the payloads, 55% were RedLine Password Stealer, 17% were a VirusTotal Uploader tool, 6.5% were Amadey Stealer. The remaining samples were insignificantly split. Due to this disparity in the distribution of payloads, there are two tables representing both the total and unique numbers of payloads for a given category. Table 1 displays the four most frequent payloads as mentioned, and Table 2 displays the remaining payloads.
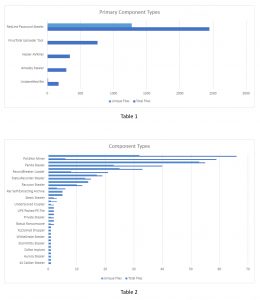
In addition to adding support for Cinoshi Stealer as a result of our RecordBreaker research, we added support for the following:
- Previously unreported malware families:
- BabyReporn Clipper: We named BabyReporn based upon a portion of its PDB filepath “C:\Users\Administrator\Desktop\vs\baby_reporn\NOCRT\Simple_trash_gen_module.pdb”. The Clipper monitors the clipboard for various BTC, LTC, ETH, TRX, DASH, DOGE, ZCASH, and RIPPLE keywords, uploading the captured data to the C2.
- StatusRecorder Stealer: While attempting to discover a name for this stealer, we discovered that user @Jane_0sint was researching the same malware, and are leveraging the naming convention agreed upon by them and @AnFam17, StatusRecorder. StatusRecorder is a fairly simple stealer which captures the following types of information: CryptoCurrency wallets, browser data from chromium and gecko, various compromised system information, Telegram, FileZilla, and Steam. StatusRecorder additionally contains a “filegrabber” module.
- XLZJoined Dropper: We named XLZJoined dropper based upon it’s usage of LZNT1 compression (optional dependent upon a configuration flag) and XOR encryption for embedded components. XLZJoined can contain multiple payloads, and each has it’s own configuration for setting file attributes, registry installation, and runtime parameters, among a few others.
- UX-Locker Ransomware: UX-Locker has runtime loader text such as “UX-Cryptor [Runtime] {winlocker.ru}”, where the reported domain named the ransomware. The domain appears to have been taken down between initial discovery during research and publishing of this blog.
- Private Stealer: The sample of Private Stealer observed during analysis was obfuscated using Obfuscar, a .NET obfuscator also seen leveraged with Agent Tesla, BlackGuard, and DuckLogs. When generating a report, Private Stealer decrypts and leverages the header string “
 Private Stealer – Report:”. The stealer obtains information such as passwords, credit cards, cookies, autofill, browser wallets, CryptoCurrency wallets, and the Windows Product Key.
Private Stealer – Report:”. The stealer obtains information such as passwords, credit cards, cookies, autofill, browser wallets, CryptoCurrency wallets, and the Windows Product Key.
- New ACCE support:
- PennyWise Stealer, reported on by Cyble.
- Panda Stealer, reported on by Trend Micro.
- Ares Loader, reported on by numerous entities, and consolidated by Malpedia.
- BlackGuard Stealer, with consolidated reporting on Malpedia.
- Open-Source malware Umbral Stealer.
The following are exemplars for the RecordBreaker loader variant and new ACCE modules:
- RecordBreaker + Cinoshi: 81cf99b843a80b9a52e7405999e78889
- RecordBreaker + BabyReporn: 8f589ce9b9227edbf48c5aca21aa8805
- RecordBreaker + XLZJoined: 5a4fc1813bf5b74e54a16241047e151a
- RecordBreaker + UX-Locker: aca3f57c858a79bc8e4e671084b0b0c9
- RecordBreaker + Private: f1e785b285c0a40760a15166a97558b4
- RecordBreaker + PennyWise: fc4843f1ba6e48ea108dba08b868facd
- RecordBreaker + Panda: 03dc9773d26b6134f2165d79ce14575c
- RecordBreaker + Ares: e23f2a40d3ed1c031b54222e36a78322
- RecordBreaker + BlackGuard: c5b1b33b905632187b2e32778cfddc9f
- RecordBreaker + Umbral: 0cf7a1a86cc177393f09fd5a4f4469fb
We have additionally added the RecordBreaker.Loader hashes and extracted socket addresses, addresses, and URLs to our acce_iocs GitHub.
